Introduction
Deprecation of Basic Authentication in Office 365 (Exchange Online) is near. Microsoft has been announcing this for a long time, and now it has finally happened. But what exactly does this mean for customers? Who is affected? In this article we explain the situation in detail, who is affected by this change (and who is not) and what you can do to ensure that this global shutdown does not cause any problems for you.
What exactly is “Basic Authentication”?
In simple terms, basic authentication is logging in with just a user name and password. There is no need for an additional logon factor, for example SMS code or confirmation by an additional action on the mobile device. Basic Authentication is often also called Legacy Authentication. This choice of words (consciously or unconsciously) emphasizes the age of this method. The following image illustrates the authentication process schematically. Of course, an extra login server could be interposed, for example an Active Directory Domain Controller, but the principle remains unchanged:
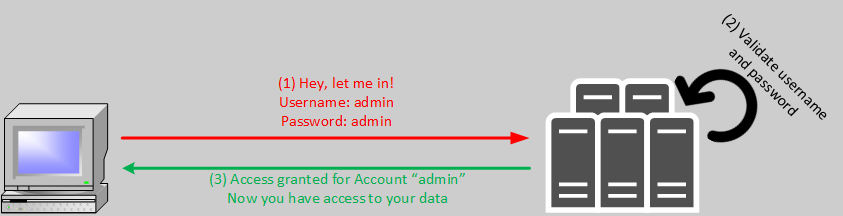
People are used to logging in with a user name and password, something that is used in many situations. These are, for example, access to webmail services, shopping portals or other online services. Things that we are used to, because they are widely used, often become the target of hacker attacks (targeted and untargeted). And that’s exactly what makes them problematic. Because Basic Authentication has also suffered this fate (for many years now). This results in several vulnerabilities of the widely deployed Basic Authentication:
- Users prevent “forgotten passwords” through Post-Its.
- Passwords are often terms from the user’s personal life, such as the name of their partner/spouse, their children, or their favorite free time activity.
- If a complex password is required, birthdays, anniversaries and similar dates are integrated into the above pattern. However, these are often easy to guess or to learn through social engineering.
- Passwords are regularly reused on multiple portals and services.
- Logins can very often be cracked by guessing or trial and error.
- Accounts are sometimes available free of charge on Internet sites. These often do not work or no longer work.
- However, accounts are also available for purchase. These even come with a guaranteed percentage of working records. Here, the purchase price for hundreds or thousands of accesses is often in the low Euro range!
In recent years, we have been educated not to reuse passwords on the one hand, and to choose complex passwords on the other. The most common rules:
- Minimum 8 characters
- Small and capital letters
- Numbers
- Special characters
Admittedly, passwords generated in this way have a good complexity in principle. However, the password expiration policy then comes into play, which again quite skillfully undermines the principle, although the originator of the expiration policy had good intentions. The supposedly secure password Sommer2023! thus quickly becomes Sommer2023!1, Sommer2023!2, Sommer2023!3, and so on, when the change is forced.
As a result, companies have often further tightened complexity policies, for example to 12 or 15 characters. The result as a result is very often the Post-It, because no one can remember the complex passwords anymore. So the risk of an unauthorized person making use of the credentials is extremely high.

But even with good, complex or unique passwords, the credentials can be at risk even without Post-It, especially if the provider has implemented insufficient security measures. In other words, the best password is of no use if the provider is compromised. A very prominent example of this is the hack of the Sony Playstation Network. If such a user database is stolen, it is usually offered for sale on the Darknet or Deep Web shortly afterwards. In one fell swoop, many (sometimes millions of) verified and working credentials are distributed.
 |
Losing login credentials very quickly puts you in the realm of identity theft. This is especially the case if credentials have been used multiple times, for example, for online shopping, email access and other portals. |
If this theft occurs in the corporate context (directly or indirectly through a scenario above), the attacker has access to a significant number of systems and the data stored on them, for example user drive(s), file server, CRM system, ERP, emails and more, in one strike. The damage caused by this cannot be quantified across the board, but it is often enormous.
 |
A very good source to get a clue if your own (or someone else’s) credentials were included in a stolen or hacked database is the free website https://haveibeenpawned.com. |
Microsoft has been pointing out for some time that so-called password spray attacks are part of everyday life in terms of Office 365. An impressive description of what such attacks can look like was already published in 2020: Protecting your organization against password spray attacks – Microsoft Security Blog. Microsoft has also provided figures on how big the problem of password spray attacks through basic authentication is: Breaking Password Dependencies: Challenges in the Final Mile at Microsoft – YouTube.
What exactly is “Modern Authentication”?
Since basic authentication is this insecure, it is obvious that alternatives should be created and used. The simplest approach is to add another authentication layer. Several mechanisms have become established here:
- SMS token
- Email token
- Token from an authenticator app
- Push notifications
- Biometrics
Since Basic Authentication does not support such extensions, Modern Authentication was created. Modern Authentication itself is not a new protocol, it rather describes a variety of mechanisms that enable modern and secure logon from a client to server-based services. Modern Authentication focuses on 3 important aspects:
- Authentication methods: multifactor authentication, smartcard authentication, certificate-based authentication
- Authorization methods: how MIcrosoft has implemented the standard Open Authorization (OAuth)
- Conditional Access Policies: Mobile Application Management (MAM) and Azure Active Directory (Azure AD) Conditional Access
With Modern Authentication, all these risks of Basic Authentication can be eliminated at one stroke. If you look at the 3 aspects above, it quickly becomes clear that you can establish highly complex logon processes with Modern Authentication. In order not to make it too complicated, here is a simplified diagram of how the logon process can work:
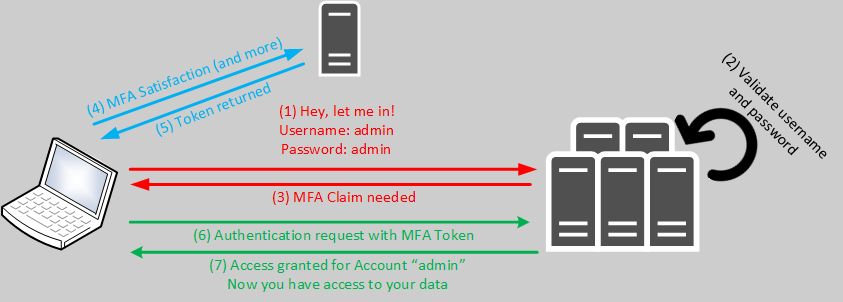
At first glance, you can see that username and password are not necessarily accepted as the only criteria. This would be technically possible, but it doesn’t make sense because otherwise you have no added value compared to Basic Authentication. So step number 4 comes into play. In the case of Azure Active Directory, several things can take effect here, for example:
- Login with OAuth2
- Confirmation of another factor (for example, in the Authenticator app on the cell phone).
- Login from an Intune-managed device
- Login from an approved location
With these additions, an additional (often even very simple) protection of the logins is possible. Azure AD also supports other things, such as the detection of so-called risky SignIns and Users at risk. However, these functionalities are not part of this article.
Why wasn’t Modern Authentication enforced earlier?
Now, of course, the question arises why Microsoft did not retire Basic Authentication earlier – and allowed such insecure protocols for such a long time. Regardless of the recurring appeals from Microsoft for more than 3 years, the sluggish support of many applications is the main reason. There are still innumerable applications that can handle nothing else than Basic Authentication. Very often you can even find Just-In-Time applications in the production sector, which are solely based on IMAP4 and POP3 with username and password as login criteria.
If Microsoft does not postpone the date at short notice (fortunately, it does not look like it), then this will soon be the end.
To what extent am I affected by the shutdown?
What exactly is being shut down?
As already mentioned several times: Basic Authentication in Exchange Online. In other words, the way users (and service accounts) log on to their mailbox and other mailboxes. In Exchange Online, the following functions are affected by this:
- Exchange Active Sync (EAS)
- POP3
- IMAP4
- Remote PowerShell
- Exchange Web Services (EWS)
- Offline Address Book (OAB)
- Outlook for Windows
- Outlook for Mac
Is only Exchange Online in focus or also other services?
Microsoft actually disables Basic Authentication only in Exchange Online. All other services already support Modern Authentication! Long-time administrators surely remember the complex configuration between Skype for Business (with Modern Authentication) and Exchange Online.
Another very important point: No automatic Exchange on-premises update will be rolled out on 01.10.2022, which would also apply this change to customer deployments. Of course, it is not impossible that Microsoft will also redact Basic Authentication on-premises with one of the upcoming CUs, but this is currently not the case.
Is my tenant affected?
Fortunately, it is now very easy to check whether your own tenant is affected by the shutdown. For this purpose, a report is available in Azure Active Directory, which evaluates the logon protocols:

Ideally, this report will not return any results (as in the image above). In this case you can relax and let the shutdown happen. Nevertheless, please keep an eye on this report, to avoid that a client sneaks in through a configuration gap.
Of course, you can also query the Basic Authentication login via an Azure LogAnalytics workbook, but the AAD report has made this necessity obsolete (especially since Azure LogAnalytics costs money, unlike the AAD Sign-In Logs report).
In any case, it is also advisable (especially for older tenants) to take a look at the Exchange Online configuration – this can be queried very easily via PowerShell:
The result of this query should be True:
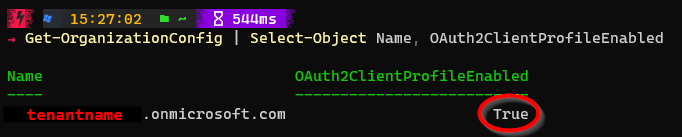
I am affected – what do I have to do?
Exchange Online general
If the PowerShell query returned False, you can very easily enable Modern Authentication (note: this does not enforce Modern Authentication, it just enables the ability to use it):
SMTP
If you have the “SMTP Relay” scenario in use, which is recommended by Microsoft and consultants in many scenarios (for example when sending mails from multifunction devices), then the good news is: There is nothing to do here with regard to 01.10.2022!
Microsoft describes 3 SMTP scenarios that are possible:
- SMTP Authentication
- Direct Send
- SMTP Relay via connector
You can read about these implementation scenarios in detail in the official documentation: How to set up a multifunction device or application to send email using Microsoft 365 or Office 365 | Microsoft Docs.
Only the first scenario actually uses credentials. Thus, this would be affected by the changeover. However, there is a special feature to note here, which Microsoft grants to customers (Basic Authentication and Exchange Online – September 2021 Update – Microsoft Tech Community):
SMTP Auth shutdown yes or no?
“We’re going to continue to disable SMTP AUTH for tenants who don’t use it, but we will not be changing the configuration of any tenant who does. We can’t tell though if the usage we see is valid or not, that’s down to you to determine. So you still should move away from using Basic and SMTP AUTH though if you can, as it does leave you exposed.”
Microsoft is keeping SMTP AUTH “open”, because it is still too heavily in use. SMTP AUTH is the only exception to disabling Basic Authentication. Microsoft disables it only in tenants where it is not in use. However, this is no reason to sit back and smile if SMTP AUTH is actually in use. Because with this you have created another intrusion gate in your tenant! The danger should not be underestimated. We strongly recommend every tenant owner to switch to secure methods, for example the connector approach (SMTP Relay) or another individual solution that offers secure authentication options, for example using the Graph API. We can support you with the changeover and securing, do not hesitate to contact us.
PowerShell
For many Exchange Online administrators, the following commands are second nature:
‘legacy’ logon in Exchange Online
$AdminCredential = Get-Credential $session = New-PsSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $AdminCredential -Authentication Basic -AllowRedirection Import-PSSession $Session -AllowClobber
This way of login can be completely erased from memory (therefore also not retrievable as gist 😉). The unsafe hint -Authentication Basic- is included here already. In addition, there is the so-called ‘Exchange Online PowerShell with MFA’, which could be started via the Exchange Online Admin Center:
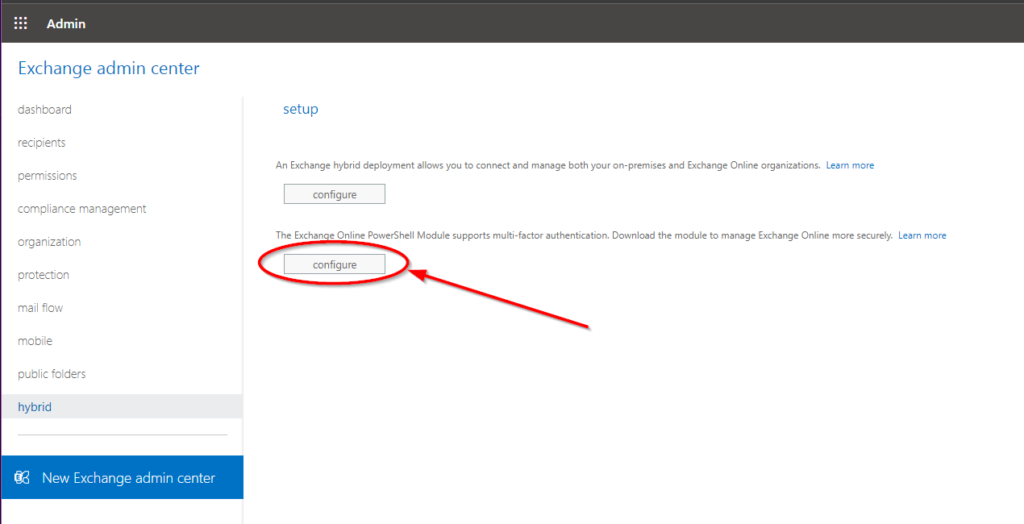
It is, of course, highly inconvenient to first log into the classic Exchange Online Admin Center to open an MFA-protected PowerShell session. Fortunately, you don’t have to worry about this anymore either, as this way will no longer be supported after Aug 31, 2022 and will be officially retired on Dec 31, 2022: Message center – Microsoft 365 admin center.
The solution is very simple: all scripts that interact with Exchange Online must be updated to the EXO V2 module. The installation of this module from the PowerShell Gallery can be done with a simple script:
In the productively used PowerShell script, only the connection establishment to Exchange Online must be adjusted. Instead of entering credentials, this command can be used:
Connect-ExchangeOnline -UserPrincipalName myAdmin@mytenant.onmicrosoft.comFurthermore, EXO V2 offers other advantages such as app authentication for unattended scripts. This completely eliminates the need for account-based logins, and regular hygiene measures (such as disabling POP3 and IMAP4 on all mailboxes) can be performed regularly without user credentials.
Exchange Active Sync
Exchange Active Sync is an old protocol for retrieving emails on mobile devices. The mail client built into Windows also supported this for a while. The approach recommended by Microsoft is to switch to the Outlook Mobile app. Not only does this support Modern Authentication, it can also be protected by MAM policies.
For the case of Exchange Active Sync (EAS) connections, there is a very simple solution:
- Switch the app on mobile devices to Outlook Mobile
- If one of the protocols EAS, POP3 or IMAP is configured in the existing MDM solution, new mail profiles must be distributed to the users
Disabling Exchange Active Sync can be done at the mailbox level, an example for this can be found in the following chapter together with POP3 and IMAP4.
POP3 & IMAP4
For these two protocols, Microsoft has released an extension that enables authentication via OAuth2: Announcing OAuth 2.0 Client Credentials Flow support for POP and IMAP protocols in Exchange Online – Microsoft Tech Community.
However, this is only recommended to a limited extent. Although many applications can be converted in this way with little programming effort, POP3 and IMAP4 are very old protocols. In the Microsoft 365 world, it is advisable to use modern and secure technologies such as Microsoft Graph to retrieve emails. This API can be used to easily check a mailbox for new emails and retrieve / export them. A simple example can be found on GitHub.
Basically, it is recommended to disable POP3, IMAP4 and Exchange Active Sync on all mailboxes where it is not needed. We offer a simple script template for this purpose as well:
See also the presentation of Andreas Hähnel at PSConfEU 2022, here you will see a live demonstration that the export of emails into any format (here XML) with the Microsoft Graph is done within a few seconds script runtime:
Outlook for Windows & Mac
Outlook from version 2013 onwards can use Modern Authentication. Basically, it is of course recommended to use the latest version of Microsoft 365 Apps for Business or Microsoft 365 Apps for Enterprise. Older Outlook versions must be updated as a preparatory measure. Outlook 2013 can be made fit for Modern Authentication via registry key:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Exchange]
"AlwaysUseMSOAuthForAutoDiscover"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common]
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Identity]
"EnableADAL"=dword:00000001
"Version"=dword:00000001All Outlook versions from 2016 onwards support Modern Authentication without any configuration effort. To make sure that a client is connected using Modern Authentication, you can take a look at the connection status (Ctrl + right-click on the Outlook icon in the Windows system tray and then Connection Status). Here Outlook shows whether it is logged in with Basic Authentication or Modern Authentication:
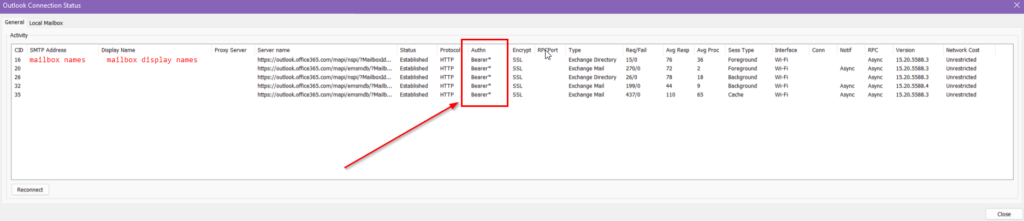
The final step – globally blocking Basic Authentication
To permanently ban Basic Authentication from a tenant, a two-step approach is recommended:
- Disable Basic Authentication with Conditional Access
- Disable Basic Authentication globally (tenant-level)
As an alternative to Conditional Access, the so-called Security Defaults can be used. These enforce Modern Authentication globally and in the same breath require all users to set up Multifactor. However, the rollout of MFA is a separate project in many companies. Likewise, activated security defaults prevent the use of conditional access. However, this is required for other control mechanisms, so the Security Defaults can only be recommended as a measure to a limited extent.
Disable Basic Authentication with Conditional Access
In Azure Active Directory, Conditional Access can be used to completely prevent logins via Basic Authentication. The advantage of this measure is that it is possible to work with exceptions. A test is also easy to perform (through the WhatIf functionality of Conditional Access). The necessary policy is created very easily. Only 2 checkboxes have to be set and the potential exceptions have to be defined:
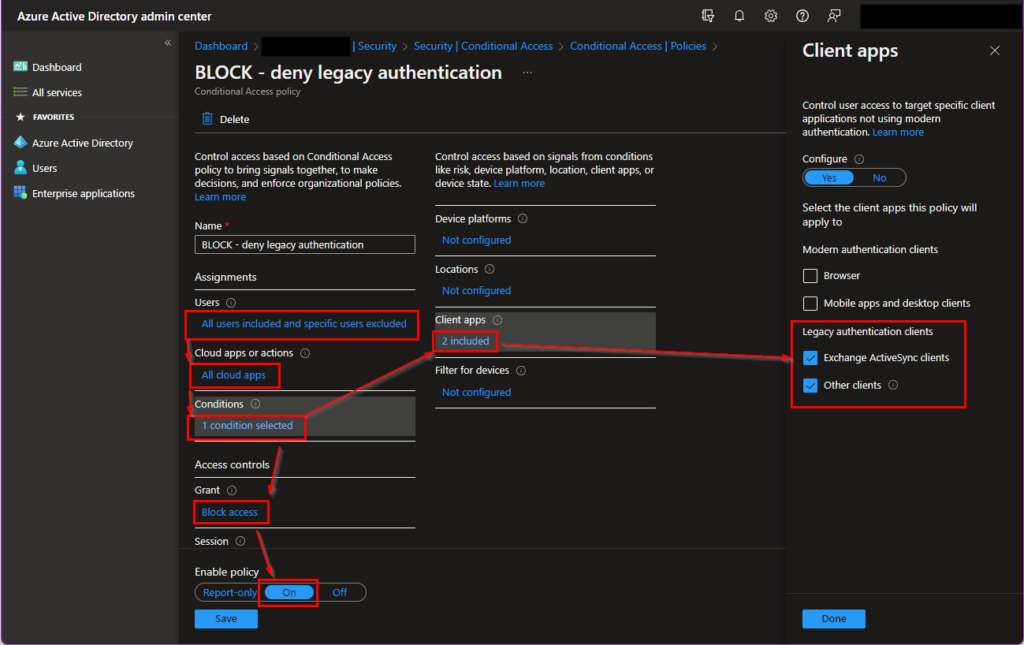
The exceptions can be users who cannot be switched to Modern Authentication yet for technical or organizational reasons, who still have to rely on the old method until October 1st, 2022. After this rule is active, it filters out all ‘legacy’ logins, so you get a very good feeling very quickly (also based on the feedback of the forgotten users) if there is still work to do before the shutdown or if you have forgotten something.
Disable Basic Authentication globally (tenant-level)
If the preparations using Conditional Access are complete and there are no more logins using Basic Authentication, you can start the global deactivation. This is done in the Microsoft 365 Admin Center under Services section. Here, too, a gradation is possible that allows Basic Authentication to be selectively disabled:
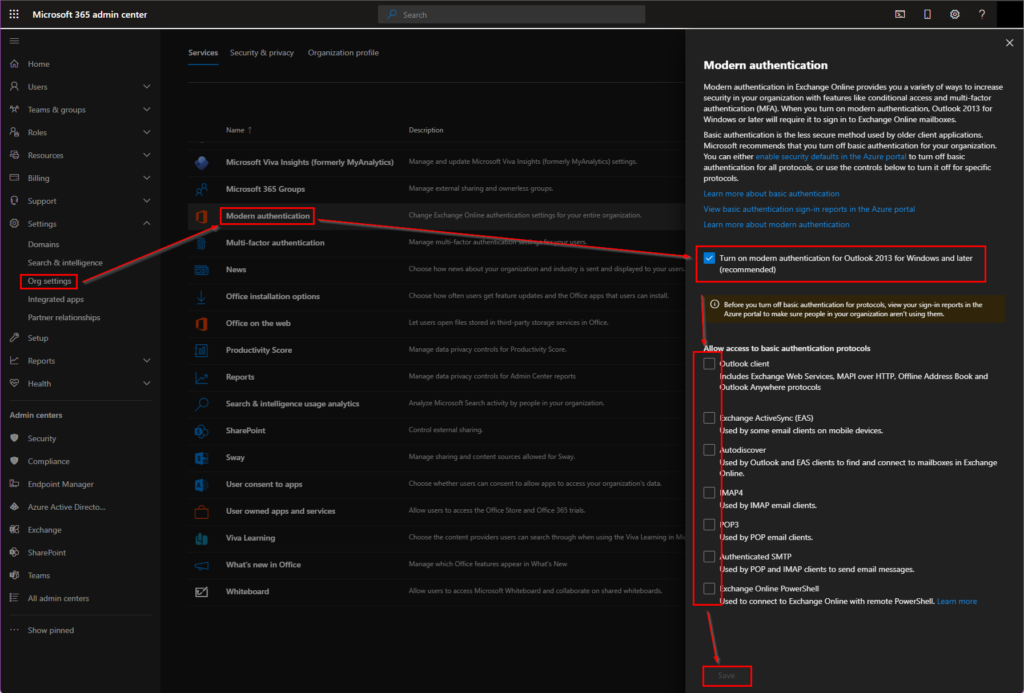
I cannot disable Basic Authentication in my tenant at the moment. What can I do?
Since September 1st, 2022, Microsoft offers a very last temporary workaround. If the shutdown on October 1st is problematic in your tenant for technical reasons, you can apply for a one-time final deadline extension until Jan. 01, 2023. To do this, you must follow this link, which opens a self-diagnosis test (by pre-filling a keyword in the help): https://aka.ms/PillarEXOBasicAuth.
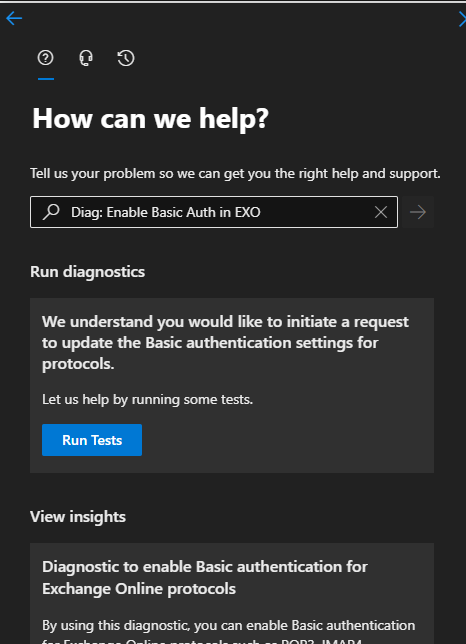
Clicking on Run Tests will start the self-test. You will be given the option to opt-out during September. This allows you to individually delay the shutdown to next year. This test will also be available after October 01, 2022. This gives customers the opportunity to specifically revert the shutdown carried out by Microsoft.
In the latest article from Microsoft, this procedure is described with screenshots. However, this approach is not recommended (with reference to the previously mentioned security vulnerabilities).
In the same breath, Microsoft has also announced to block Basic Authentication queries in the Microsoft 365 apps. This doesn’t really make the difference, but it does round out the overall picture.
I need assistance – who can help me?
We help you with your upgrade to Modern Authentication and securing your tenant – book your individual consultation appointment today to determine to what extent you will be directly affected by the shutdown and how you can avoid problems from October 1st, 2022:
Further assistance is also possible, please feel free to contact us without obligation!
Related links
Improving Security – Together – Microsoft Tech Community
One simple action you can take to prevent 99.9 percent of attacks on your accounts (microsoft.com)
Deprecation of Basic authentication in Exchange Online | Microsoft Docs
Authenticate an IMAP, POP or SMTP connection using OAuth | Microsoft Docs
Basic Auth and Exchange Online – February 2020 Update – Microsoft Tech Community
Basic Authentication and Exchange Online – September 2021 Update – Microsoft Tech Community
Basic Authentication Deprecation in Exchange Online – May 2022 Update – Microsoft Tech Community
Enable or disable modern authentication for Outlook in Exchange Online | Microsoft Docs
Protecting your organization against password spray attacks – Microsoft Security Blog
Wikipedia:10,000 most common passwords – Wikipedia
Password-less strategy – Windows security | Microsoft Docs
Why a PIN is better than an online password (Windows) – Windows security | Microsoft Docs




