Introduction
Friday the 13th is commonly known as unlucky day – on Friday, Jan. 13, 2023, an update with ASR malfunction made sure this day lived up to its reputation. Version 1.381.2140.0 of the Defender Security Update contained a bug that caused the Attack Surface Reduction (ASR) component of Microsoft Defender to delete or render unusable shortcuts (.lnk) on countless Windows clients worldwide. Microsoft was relatively quick to confirm this issue on its Twitter channel. The response from admins worldwide ranged from schadenfreude to horror and many comments along the lines of quality assurance. In the end, this faulty update resulted in Start menus and taskbars often looking like this or similar:

Protection History also confirms this, citing ASR as the source:
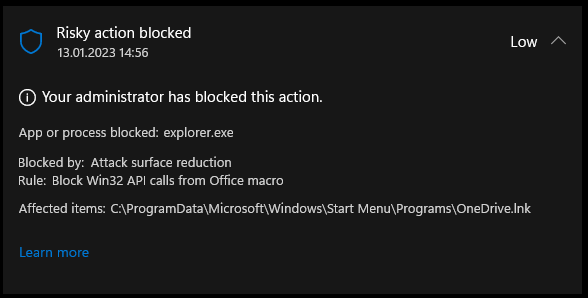
The hashtag #ASRmageddon also quickly spread across social media. The official workaround was to set the Block Win32 API calls from Office macro function described above to Audit and force the synchronization of Intune-managed devices – in the hope that you yourself would be spared. Nevertheless, many millions of devices were affected. Now the question remains how to restore the missing shortcuts on all your corporate devices.
General
The ASR malfunction has been fixed in the meantime, so all devices should be forced to update Defender immediately. This can be done via Intune, for example.
How badly is my company affected?
You can evaluate this via the Advanced Hunting functionality in the Defender Portal – Microsoft has provided a query. The first query identifies all devices that are affected by the rule, since the rule runs in “block” mode:
DeviceEvents
| where Timestamp > datetime(2023-01-14)
| where ActionType contains "AsrOfficeMacroWin32ApiCallsBlocked"
| extend JSON = parse_json(AdditionalFields)
| extend isAudit = tostring(JSON.IsAudit)
| where isAudit == "false"
| summarize by Timestamp, DeviceId, FileName, FolderPath, ActionType, AdditionalFields, isAudit
| sort by Timestamp ascHowever, there is no way to granularly identify the links that were broken by AsR – at least there is no information on this from Microsoft.
Option 1a – The script-based solution approach from Microsoft
Microsoft has published a workaround on its Twitter account. This can be found at https://aka.ms/asrfprecovery. The link leads to a Techcommunity article. Here Microsoft provides a PowerShell script that is supposed to help companies to restore the links automatically. This script restores often used links. However, this script has several weaknesses:
- it runs only “as administrator” – not every user is allowed to run it.
- it restores only heavily used links, like Adobe Reader, Office programs, notepad++ and so on. Other, custom links do not.
- It does not restore the taskbar shortcuts.
So the script is only really useful in certain use cases.
The community was quicker than Microsoft in this regard. Already a few hours after the ASR malfunction became known, articles like this one appeared on the web, which have a very similar quick-fix approach.
Option 1b – the manual approach of Microsoft through installation repair
Microsoft also explains in the above article that the repair function of the installers can also restore the shortcuts. However, this option can be very time-consuming and is only recommended if a client needs to be repaired manually very quickly due to the ASR malfunction.
Option 2 – Recovery via GPO or Intune Policy
Once the links are standardized across the enterprise, they can be re-rolled across the enterprise via GPO or Intune Policy: Configure and customize Windows 11 taskbar – Configure Windows | Microsoft Learn. This helps many at least for a subset of devices, for example if there are different categories of devices in use that have standardized layouts that users are not allowed to customize.
Option 3 – Windows Restore Point
There is the possibility to reset Windows to a Restore Point, for example to a point on 12.01.2023, when all shortcuts were still functional. The prerequisite is that such a Restore Point exists. The restore requires manual input, but can be triggered automatically. The manual process is documented here. There are numerous other blog articles on the net (like this one) which describe the procedure in an illustrated manner.
Since user interaction is required, this option is also feasible as a solution to ASR malfunction only for selected groups of users and devices.
Option 4 – manual recovery
Also very time-consuming, but easier to implement than Windows recovery is the creation of the links in the folders. All Start Menu shortcuts for Windows 11 are located in the C:\ProgramData\Microsoft\Windows\Start Menu\Programs folder. All taskbar shortcuts for Windows 11 are located in the folder C:\Users\<USERNAME>\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar.
This variant as a response to the ASR malfunction is also complex, but can quickly lead to success for experienced users.
Option 5 – Restore from client backup
If you have a client backup in use, you can restore the shortcuts from the backup. Here again the two folders already mentioned above are relevant:
Startmenu: C:\ProgramData\Microsoft\Windows\Start Menu\Programs
Task bar: C:\Users\<USERNAME>\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\
Many backup solutions allow automation. From this point of view, currently the best option is to restore the missing links that the ASR malfunction has rendered unusable or deleted. Our tests have shown that this is also the most stable option (besides the system restore). Only several linked Edge profiles are problematic, all other shortcuts were restored flawlessly. Since the use of Edge profiles is often rather the exception, or used by administrators, the impact is no longer as dramatic as with other solutions.
The result of our tests is that indeed only the Edge profiles are missing and the Start menu is complete again:

All restored shortcuts were fully functional after recovery. Only the Edge profile shortcuts remained. These had to be recreated.
Conclusion
Defender’s faux pas on 13.01. impressively demonstrated that an error at a service provider can have a negative global impact. Fortunately, such errors do not happen very often, but they do happen. Very often, customers assume that the service provider will do the work completely and can also restore everything – this is wrong, as this case shows. There is no recycle bin for an ASR malfunction, otherwise the links would be easily recoverable. It is the responsibility of every customer to back up their data themselves so that they can restore it.
Black Magic Cloud offers solutions from Acronis for this purpose, with which we were able to achieve very good results, as described in the article above. Would you also like to secure your clients and / or cloud solutions against accidental deletion? We would be happy to advise you on the power of the Acronis solution:




