Introduction
Sharing in Microsoft 365 is an important matter. With Microsoft 365, Microsoft has created an ecosystem for virtually borderless collaboration with external participants. But what exactly is the difference between guests and external participants? When do I use a team, when OneDrive, when SharePoint? This article provides answers to these questions.
End users don’t want to deal with complicated decision matrices, processes or mind games. They want a simple way to share their files or information with the “other party” – whether internal or external. Of course, this desire is absolutely understandable. However, this is very often countered by a desire on the part of the company:
The company’s data and information must be protected against unauthorized access.
Of course, this demand is absolutely understandable. No company wants to risk its sensitive data falling into the hands of others. So that you can define the appropriate options and ways of sharing for your company, we explain the most important basics in this article.
Externals or guests?
Sooner or later, virtually every user has to master this challenge when a conversation is to be started with a person who does not have an internal account in their own Microsoft 365 tenant. In the Teams search, you start typing the name and eventually get a result like this or very similar:
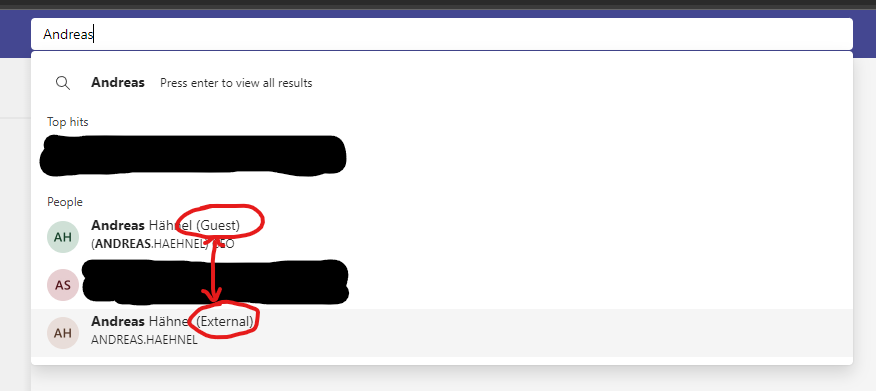
Behind both users hides the same person, but technically a different account. Even if the chance of catching the right or wrong one is statistically 50:50, Murphy’s Law has shown that you almost always catch the wrong one. So: which one is the right one? To answer this, the difference between guest and external must be clear:
External – this account is outside the tenant’s own environment. If information is sent to this account, this information leaves its home environment and is no longer protected by the security mechanisms of its own IT.
Guest – this account originally comes from a foreign tenant, but was invited into the own tenant. The source account is still outside the own infrastructure, but the guest is managed (at least partially) in the own environment. If information is sent to this account, then this information does NOT leave the own environment and thus falls under the security mechanisms of your own IT.
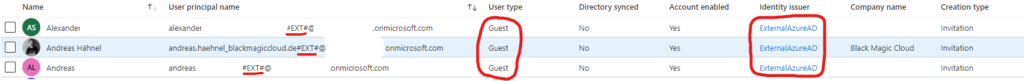
A guest user is very easy to identify in Azure AD, it is administratively displayed this way:
Anonymous users
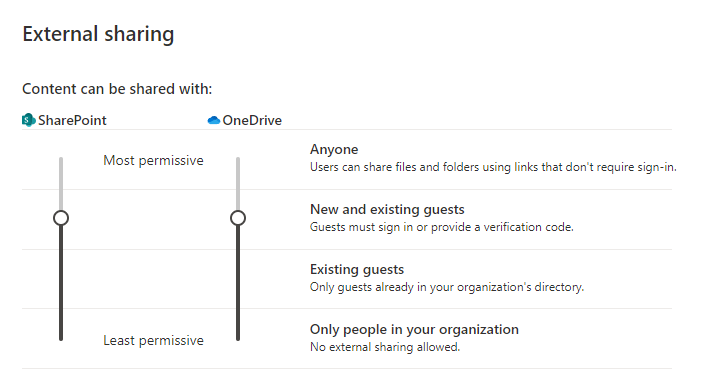
In addition to guests and externals, there is sometimes the user type Anonymous. This user type is an external who is allowed to access shared information and files without authentication. This type of sharing can make sense (for example, to publish a product brochure or flyer), but is absolutely unsuitable for most work documents and information. Anonymous users should always be completely disabled by default. This can be done in the SharePoint Admin Center:
Sharing via teams
As the name suggests, Teams are meant for any kind of working groups, project groups and similar. They can be filled with both internal and external employees. Teams can be organized with channels for better sharing of information. Channels can also provide access protection through their different types. For example, all data freely accessible to the team is stored in public channels, all sensitive data in private channels and others in shared channels.
Teams are excellent for working in a group. But they are not suitable for one-time exchanges. This would make exorbitant growth and orphaned Teams in a tenant. So OneDrive or SharePoint is the better choice here.
Sharing via OneDrive for Business
OneDrive for Business is a user’s personal cloud storage and usually 1 TB in size. That’s a lot of space for all sorts of data that could also be shared with external contacts.
However, the danger of sharing too much is very high. In everyday stress, it happens very quickly that instead of sharing 1 file, you share a whole folder with others. Thus, you have potentially allowed unauthorized access to data that they should never have seen. Also the risk is very high that a folder has been shared in the past, but the exact settings have been forgotten, and now data is mistakenly stored in this folder. This also gives the external party access to information and files that were never intended for them.
Sharing with Anonymous is even more dangerous in the scenarios just shown, so it should not be considered.
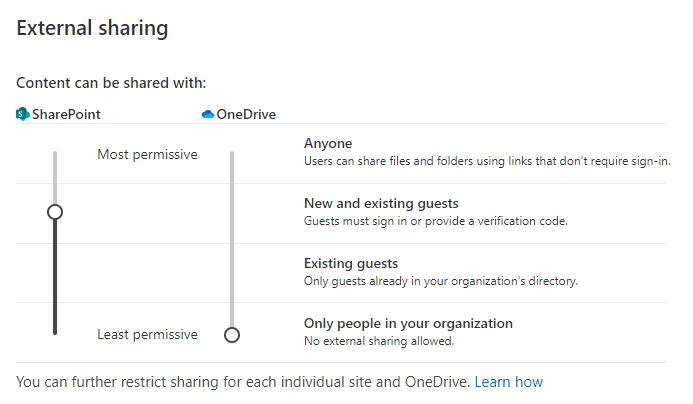
Since OneDrive for Business is intended for personal work, you should avoid storing and sharing team-relevant information and documents here. OneDrive for Business should only be used internally. This means for the sharing settings:
There are other sharing settings in the SharePoint Admin Center that can be configured as desired, such as limiting sharing to specific recipient domains. This in turn requires an internal approval workflow, which unnecessarily drags out potentially urgent requests. Administrative overhead also increases.
If Teams and OneDrive aren’t an option for sharing, SharePoint Online remains. SharePoint is designed for group and project work. But it also offers the same hidden dangers as OneDrive for Business:
- unintentionally share too much at once
- unintentionally share through already existing shares
If an existing library or folder is to be shared with an external party, then you are in the scenario that used to be called an extranet. This scenario is perfectly feasible, but clearly defined and established governance processes are an absolute must here. Otherwise, the danger of unintentionally sharing too much is omnipresent here as well.
In order to create time-limited and/or controllable sharing platforms that prevent the problem case of “too much shared” through automatic deletion, it is possible to switch to third-party providers. However, this carries the risk of passing on your data to another third party, with the additional risk of data leakage here. To eliminate this risk, such an exchange platform can be set up with myMagicShare. This ensures that the data can only be accessed by a defined group of people within a defined period of time.
Information protection (with Azure Information Protection)
Any document can be protected via Azure Information Protection. AIP prevents unauthorized people from opening a document. However, AIP requires a large-scale implementation project and a lot of training. In principle, AIP can be recommended to any company, but only if it is implemented properly. AIP-protected documents can be shared easily via myMagicShare.




