Introduction
Christmas is known to be the time when you give yourself a crazy amount of gifts. The anticipation is increased by opening a door every day after getting up and being excited about the gift. In 2022, we’ll also be opening a little door every day in our digital Advent calendar. Behind each of these doors is a small gift for the community. It’s always valuable knowledge and also great tips and tricks. The areas covered are also very diverse:
- Microsoft Teams
- PowerShell
- Microsoft Graph (with PowerShell)
- Microsoft 365 general
- Microsoft Azure
- and many more
We wish everyone a reflective Advent season and much anticipation for the gifts that are coming 🎁🎄🎅.

Door 1 (01.12.2022) – free M365 E5 tenants for everyone!
That sounds too good to be true? But this offer really does exist – directly from Microsoft. The magic word here is Developer Tenant. These tenants are primarily intended by Microsoft for developers, but they can also be used as test or evaluation tenants. The content is a complete Microsoft 365 E5 (without Windows and audio conference) – typically Microsoft gives you 25 licenses for free. Officially, these licenses are labeled as trial licenses:

| Developer tenants must not be used productively, there is no support from Microsoft! |
Even registering your own domains can be dangerous, even if this is technically possible without any problems. Why is this so? The answer is simple: Microsoft automatically deletes inactive tenants after 90 days. If nothing has happened in the tenant during this period, your own configuration is still present and a domain is still registered. Removing it from the Microsoft backend (to use it in another tenant) is very difficult.
The really great thing about these tenants is the ability to have them created with pre-built data. Emails, SharePoint content, teams, conversations – everything is already there. So you can start your tests and developments right away and don’t have to artificially fill the new environment with life.
Where can you get such a tenant? By signing up for the Microsoft 365 Developer Program. This is free of charge. The Developer Program and the free tenant can be found here –> Developer Program | Microsoft 365 Dev Center.
Door 2 (02.12.2022) – Microsoft PowerToys
Windows is good, but not perfect. But what software is? Microsoft already had little helpers in the past that hardly anyone knew about – or do you remember a tool called Microsoft SyncToy? That was a small tool that kept data in 2 folders in sync – no matter if on your own hard drives or in the network. Back in the days of Windows 2000 and Windows XP I (Andreas) used it very much. At some point SkyDrive (the OneDrive predecessor) came and the SyncToy lost its importance.
Another example is Karl Klammer. For some he arouses positive emotions, for others not – the bottom line is that Karl was ahead of his time as a virtual assistant and today enjoys cult status. By the way: a tool that hardly anyone knows is (was) Microsoft Bob.
Even nowadays, Microsoft provides helpers. For admins, these are the well known SysInternals, which can all be downloaded directly from Microsoft here. But also for the user, Microsoft has something up its sleeve: the so-called Microsoft PowerToys. The PowerToys are a large toolbox with all sorts of small but extremely useful tools, of which we would like to briefly introduce 3.

In the screenshot above you can already see FancyZones, this is a customizable grid layout for your own monitor. In other words, you define zones in which you want to arrange your windows. Especially with large monitors, this can be used very efficiently. The layouts are flexible, so everyone can find his desired layout. In the following screenshot 3 connected screens are available, for screen 2 (with resolution 5120×1440) a layout is created:

The second ingenious tool is the so-called Image Resizer. There are hundreds (if not more) tools available for download and also websites that offer such. But why install a third-party tool when you can get it directly from the manufacturer? Exactly the same formula can be applied here. Image Resizer can resize and optimize images. Once the tool is activated, just right-click on the image you want to resize and choose which format you need, e.g. 32×32 for a thumbnail or avatar, or any other custom size:

The third tool we would like to introduce here is PowerRename. It is designed to rename several files at the same time, i.e. “in batch”. Imagine you have some files in a folder that all have the same spelling mistake, for example someone made a mistake in the accounting department and all files are called “Invoice_<date>”. Instead of sitting down and adjusting each of the many invoice files one by one, PowerRename can do it in much less time. Just select the “affected” files, right-click and select the PowerRenane menu, and have the spelling error corrected:

These 3 and many more tools are content of the PowerToys (e.g. Awake, Hosts File Editor, Screen Ruler, …). If you want more, you can download and install the PowerToys directly from Microsoft: Microsoft PowerToys | Microsoft Learn.
The PowerToys can also be installed via the command line, or even rolled out in the company via software distribution. Among others, winget and chocolatey are available here. The installation with winget:
Installation with chocolatey:
Happy testing! 🤖
Door 3 (03.12.2022) – Cloud licenses = one-way street?
The opinion is often circulated that licenses are a dead-end topic. In the past, it was often the case that customers only had one license agreement. All purchases were then processed via this contract. It did not matter whether server CAL, operating system or application (for example Exchange or SharePoint).
Nowadays – as is so often the case – the familiar patterns are outdated and therefore no longer appropriate. Microsoft has launched new licensing models, the most prominent being the (now former) C(loud) S(olution) P(rovider) model. This model was available for a few years. Typical Microsoft, everything has to change after a few years, so also this model. Now it is called NCE (New Commerce Experience). According to official statements, Microsoft’s goal is to strengthen its partners. Whether this will really happen remains to be seen, because one of the first actions was a price increase. This will also affect all other models in the medium to long term, but NCE will be the first to feel the effects.
But what about if you already have a volume license agreement (e.g. an Enterprise Agreement), are you 100% bound to it and not allowed to sign another contract? Of course, EA often offers much better prices than any other partner would be able to offer. There is also a true-up option (= reordering of licenses). This mechanism only works if there is already at least 1 such license in the contract and is bound to runtimes. If you as a customer have an EA with a remaining term of up to 3 years, but often want to be able to act more flexibly (for example, to protect against fluctuation). In this case there is the option to combine EA (or others) and NCE in one tenant. This is also possible within 1 license type. Assuming you already had 500x Office 365 E3 via EA and want to reorder 20 of these licenses for only 6 months, you can do exactly that via the NCE program. With an EA you are often much less flexible due to the remaining term.
NCE has another (for many customers very interesting) aspect: The provider from whom the licenses are purchased is, according to the contract, always the first contact (for support, faults, etc). This is often not the case when licenses are purchased through other contracts or credit card. With NCE you do not have to open a ticket with Microsoft. You can contact the MSP you trust directly.
Regarding the prices, the decisive factor for NCE is the duration. If you sign up for an annual subscription, you can assume the list prices that Microsoft publishes on its own website. Adding additional licenses is not a problem during this period, the subsequently ordered licenses are based on the period of the first purchased. With EA, the price is purely a matter of negotiation.
A brief overview NCE vs. EA – which scenario you evaluate as the most suitable for you is of course up to you:
| New Commerce Experience | Enterprise Agreement |
| >> PRO<< | |
|
+ Flexible terms (can be terminated monthly or annually) + The MSP from whom the licenses are purchased is contractually the first point of contact. + NCE can be used from companies with 1 employee (no lower or upper limit) + Some providers (e.g. Black Magic Cloud) offer a self-service portal in which each customer can order his license requirements independently. + MSPs can launch their own products based on NCE, e.g. our Full Managed Tenant offer |
+ often very competitive prices + costs are calculable due to the longer term (3-year price stability) + ensure good prices for many products by including them in the contract + Contract directly with Microsoft, without distributors in the middle |
| >> CONTRA<< | |
|
– approx. 25% higher license costs with monthly cancellation option – possible price increases hit faster, as maximum annual subscriptions are possible (1 year price stability) – Support is included, but not the service level. The required support can often only be realized through additional support contracts. |
– Flexibility in license purchase only achievable through tough negotiations – EA is available only for large customers, small companies do not get this option – good support is often only realizable through very expensive support contracts (with system houses or Microsoft) |
Typical scenarios where you mix between EA (or even other contracts like MPSA) and NCE are:
- Flexibility to guard against fluctuation
- Dissolution of the EA due to time inflexibility
- Cushioning of a period until the next true up
- Operation of a test, dev or QA environment that is not anchored in the EA.
- Desire for knowledgeable contacts and quick problem resolution rate
- Existing service relationship
- Procurement of test licenses of a new SKU not covered by the EA
By the way, anyone who orders Microsoft licenses from us by 01/31/2023 using the coupon code LICENSEXMAS22 will receive a 5% discount for the first year (or first month – depending on the term of the licenses ordered; The provisioning date may be up to 6 months in the future, so no later than 07/31/2023). This offer is valid for both cloud (M365 / Azure) and on-premises licenses.
Door 4 (04.12.2022) – When exactly was the teams call?
Teams has a very nice overview of all incoming and outgoing calls. Both landline and VoIP calls are listed as soon as you switch to the phone app:

At first glance, the list seems complete – but one important detail is missing. The list does not answer the question at what time the phone call took place. At least not at first glance:

However, retrieving the exact time is not as complicated as you might think. Just click on the desired call and the desired information appears on the right side in the Teams client. Here, the missing infios are then immediately added. Don’t worry, just clicking on an entry in the phone list will not start a call, as long as you don’t accidentally click on the “Call” button.

As you can see, all the relevant information is here:
- What was the date of the call?
- When was the call started?
- When was the call ended?
- How long did the call take?
In addition, you can see the typical interaction options of Microsoft contact cards, i.e. chat, organization chart, video call and start phone call.
Microsoft has already announced that it will improve the phone overview and upgrade these (and other) features:

Improved telephony overview.
source: https://techcommunity.microsoft.com/t5/microsoft-teams-blog/what-s-new-in-microsoft-teams-october-2022/ba-p/3666435
However, the promised improvements have not yet been rolled out in many tenants. As long as the rollout is not completed worldwide, the tip of our today’s door box remains very helpful 😎.
Door 5 (05.12.2022) – Cloud-based signatures in Outlook
Microsoft already announced this function a few years ago. Originally, the cloud-based signatures were even supposed to be rolled out in 2020. However, the function was withdrawn again for performance and stability reasons.
Now Microsoft has brought back the cloud-based signatures. From time to time, the function is also called Outlook roaming signatures. But it always means the same thing. Outlook on the desktop is hereby enabled to store signatures of a user directly in the mailbox instead of in the file system as before. The latter always had the unpleasant side effect that a user called the helpdesk shortly after changing computers to complain that all email signatures had disappeared.
With the new function, these calls are now a thing of the past. Even after the new computer is up and running, the personal email signatures are all there. None have to be recreated. The beauty of this is that IT doesn’t have to roll out a patch; the feature comes naturally. The only requirement is a mailbox in Exchange Online. On-premises mailboxes are out of luck.
However, on-premises mailboxes are not the only limitation. The following scenarios are also problematic:
- Sending from a shared mailbox
- Central specification of signature content such as banners
- Mobile devices
For these 3 use cases, there is still only 1 solution: a centrally controllable cloud-based signature solution. We officially distribute the solution Exclaimer. This solution has the immense charm that it works either with a client add-in or by routing the mails via the Exclaimer infrastructure. Contact us for a non-binding offer!
Door 6 (06.12.2022) – Remove Orphaned Users from SPO
SharePoint has always been a diva. This was the case long before cloud technologies became established and this has not changed with SharePoint Online. A very popular problem are so-called orphaned user objects – orphaned accounts in SharePoint that still exist although they have already been removed in AD or AAD.
These user accounts only hurt to a limited extent at first, but it is always unpleasant to see retired or orphaned accounts presented in views. It can become problematic when migrating content, because the user object is not really usable – it is orphaned.
To clean up your SharePoint Online, we provide a PowerShell script that identifies these user accounts and removes them from SharePoint Online. This way your own environment always stays clean!
It’s worth keeping an eye on the repo, there will be more cool little helper scripts provided here over time.
Door 7 (07.12.2022) – Improved protection for important accounts
Every company has accounts that are particularly worthy of protection. These include various key positions, such as C-level and other employees who are in the public eye. Since these people are inevitably exposed to attacks more frequently due to their presence in public, Microsoft offers the option of marking these employees as so-called priority accounts. Accounts marked in this way are then specially protected in Microsoft Defender. This special protection means:
- Adapted heuristics: This could be briefly described as “AI strikes.” Microsoft has found that the mail behavior of a supervisor is different than that of an employee. This knowledge is incorporated here, and the patterns of email behavior are applied to Priority Accounts.
- Special highlighting in reports: In Defender, priority accounts are given the identical tag and are thus visually highlighted in reports.
- Premium Mailflow Monitor: If problems occur with Priority Accounts when sending messages (delays or undeliverability), you can be alerted. In this way, business-critical processes are better monitored.
To use this feature, you need the following licenses, which you can purchase through us (if available also as a trial license) – contact us! Some technical requirements must also be met:
- Microsoft Defender for Office Plan 2 (included with Office 365 E5, Microsoft 365 E5, and Microsoft 365 E5 Security)
- Office 365 E3
- for Premium Mailflow features, there must be a total of 5,000 licenses in the tenant that provide Defender for Office functionality.
- At least 50 active users per month in one of these services: Teams, Exchange Online, OneDrive for Business, SharePoint Online, Office Apps
- Up to 250 priority accounts can be defined
The definition is very simple via the M365 Admin Center:

Here you can add these accounts via a small wizard. To make it easier for the admins, you have the option to search not only by name, but also by job title and distribution lists. Many companies maintain distribution lists for functional levels, so this function makes a lot of sense.
In Defender itself, the function should also be enabled. This is done in the area Settings -> Email & Collaboration -> Priority account protection:
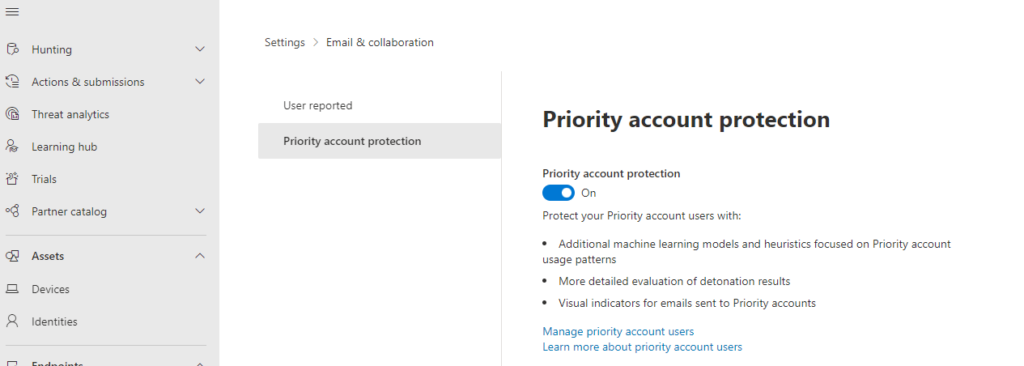
As a result, the priority accounts are highlighted in the Defender reports, which makes it possible to quickly identify the email traffic of the priority accounts. The highlighting is also very helpful in the case of attempted attacks, as well as in the details of entries in the log.

The red label “Priority Account” literally jumps out at you, as does the overview. This gives the admin a good, quick overview of whether the accounts are under attack and can derive further measures, such as raising awareness among those affected or tightening up the technical measures.
Door 8 (08.12.2022) – OneDrive Shortcuts
OneDrive is an ingenious tool for taking OneDrive and SharePoint files with you for offline editing. Since it’s also possible to synchronize SharePoint libraries, you’ll quickly accumulate a few entries in the OneDrive client that need to be synchronized. This in itself is nothing objectionable – on the contrary. It always gets exciting when changing computers. Then questions arise like:
- OMG, where was the SharePoint site?
- Why can’t the OneDrive move it automatically?
The latter could be done with a little programming effort, but you can save yourself the effort. OneDrive has an ingenious feature – namely the shortcuts in OneDrive. These can be set in any document library:

Now OneDrive creates a link in the root directory of your own OneDrive. The big advantage of this method: OneDrive is synchronized anyway, the shortcut is now automatically included, you are no longer forced to add the SharePoint libraries individually for synchronization! This procedure prevents exactly the above questions.
The great thing about this is that the shortcuts can be sorted. It is therefore a good idea to create another folder in OneDrive into which you can move the shortcuts. This way you can quickly sort your shortcuts. Shortcut folders are also highlighted by their own icon and are easily recognizable as such:
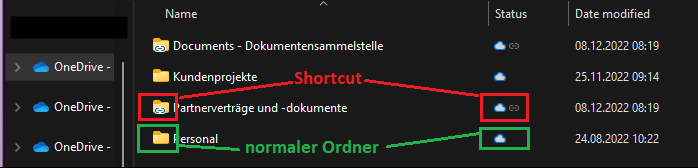
This trick is not only helpful when changing computers, but also when synchronizing OneDrive on multiple devices. Because then the data is the same on each device.
And what happens if you no longer need a link? Simply delete it from your OneDrive, the source (i.e. the SharePoint page and its content) remains untouched.
Door 9 (09.12.2022) – DevToys
A few days ago we reported about the PowerToys – but there is another ingenious tool: the DevToys! The DevToys are an immense collection of converters, coders, formatters, generators, text tools and graphic helpers that every developer needs again and again – no matter if beginner or longtime pro. As with the PowerToys, we would like to introduce 2 tools in more detail.
The first one is the Lorem Ipsum Generator. With this you can – as the name suggests – create a dummy text of almost any length (this is not only interesting for developers!). For example, if you have a document template that you want to give artificial life to, this tool is just the thing. It is enough to set the length and type of the desired text and you will get a usable result. In this example a dummy text with 10 paragraphs:

The second handy tool is the so-called Colour Picker & Contrast. This helps every developer and designer to assess the readability of their design based on the Web Content Accessibility Guidelines standard:

As you can see in the screenshot, the same color scheme is not ideal for all font sizes. However, such things are often forgotten – there are dozens of examples on the Internet.
Now the question remains: Where do you get the DevToys? Again, there are several options. The first is directly via the Windows Store as an app. But also as with the PowerToys, the DevToys can be distributed via modern software distributions in the company via winget:
Those who already use choco as a software distribution can of course also fall back on this:
Door 10 (10.12.2022) – Restrict Azure AD Tenant Creation by User
Azure AD holds a lot of settings that regulate what a user can and cannot do in a tenant. A very new setting is the following:

| Spoiler: We recommend to disable that feature! |
But what exactly is behind it? This switch determines whether each employee may create AAD or AAD-B2C tenants for himself. This tenant creation is done via the primary login of the actual tenant – in other words, with the company’s login name. Any employee can do this easily via the Azure AD Portal. Here, a button called Manage tenants is hidden:

If the user clicks on this, they can create another tenant for themselves by going through the normal creation process. First, the user is asked whether an AAD or AAD B2C tenant should be created, then a name must be assigned and the storage location must be specified:

After confirming a captcha and waiting a few minutes, the tenant was created. The administration of the company does not receive any information about this! The creator is automatically registered in this tenant as a guest with global admin rights. The company administrators do not have access to this tenant and do not see it in the overview. For this reason, we recommend disabling this function.
However, there are situations in which a subtenant makes sense. This would be for example when developers need a test environment and a dev-tenant (see door 1) is not a suitable means or a detached test environment. For these cases, our recommendation is:
| Sub-tenants should be specified by the central administration. A process can be established here. The requesting user can be added after creation via the AAD guest invitation process with appropriate rights. |
In this way, the following is ensured:
- there is no uncontrolled growth
- Naming conventions can be enforced
- In the event of an emergency, a tenant can be quickly deleted centrally (or – if possible – can still be saved).
- You don’t have to deprive users of this feature, but it adapts to the company and processes
- One has controllable test environments
The worst-case scenario that could occur by leaving it open: A user creates a connection to a third-party system in such an island tenant because their own internal tools and processes seem too complex or insufficient. So, over time, shadow IT and shadow processes are established, possibly even together with colleagues. The moment this employee leaves the company, not only is the process lost, but potentially also a lot of data (which could also be very easily extracted via such a tenant). No company wants to experience this situation, so we recommend deactivation (see above).
Door 11 (11.12.2022) – Cyber insurance
At the top of the agenda for many entrepreneurs is the topic of assessing IT risks and covering them as best as possible. Many insurers offer cyber policies to provide the best possible protection against residual risks. Many entrepreneurs have already taken out cyber insurance and feel confident that they are well covered in the event of an emergency.
We cooperate here with the company IDVS, an insurance office in Straubing. This cooperation has resulted from our membership in the kiwiko eG. IDVS is characterized by the fact that no 08/15 contracts are sold here, rather the individual customer request is in the foreground.
We hope that your broker has worked with you to tailor your cyber insurance to your individual risk profile and that your IT department and the broker have not just sent questionnaires back and forth, but that a thorough risk assessment has been carried out in advance by a specialist from the broker. If not, then we have something hidden in my doors for you today. IDVS has bundled the necessary know-how from the IT and insurance industry since 2020 and has rounded and perfected this with a high level of expertise and a lot of experience.
Nutzen Sie das Angebot der IDVS für eine kostenlose Risikoüberprüfung und melden Sie sich bei mir oder den Kollegen von IDVS.
Feel free to contact us, we will put you in touch with the right contact person at IDVS!
Door 12 (12.12.2022) – Security Baseline Part 1: Multifactor Authentication and Number Matching
It used to be perfectly normal to use one password for all your accesses. The experts always advised against it, but the world wasn’t as connected as it is today, so it wasn’t as dramatic as it is today. An attacker had to expend much more energy to compromise a user and commit identity theft.
As of today, however, it is often the case that 1 stolen password allows access to many services, for example, the Amazon account, online banking, LinkedIn, Facebook and more. This scenario is, of course, conceivably unfavorable. On the other hand, there is the challenge of having to remember an extremely large number of passwords, as each portal requires access. Very few support all the major identity providers such as Azure AD (so it would be possible to log in to a service with your private [or, if required, business] Microsoft account – assigning a new password is not necessary, authentication takes place at Microsoft in Azure AD).
To address this problem, multifactor authentication (MFA) can be used. By using MFA, the login must be confirmed, i.e. the ‘simple’ access via the combination username + password is no longer possible. Two things are problematic here:
- not all portals on the Unternet support MFA
- often MFA prompts are blindly acknowledged without questioning whether this application actually comes from oneself
Portals without MFA support should be strictly avoided according to today’s security requirements. Blindly confirming requests ultimately means allowing the attacker to access your own account. Who would open the front door in real life if a masked person stood in front of it? Certainly no one. So why do we do this at MFA?
In Azure AD, multifactor should always be active for every access. For the problem of blind confirmation, there is a very simple tool from Microsoft: Number Matching. Number Matching is very easy to configure in Azure AD and results in a user having to enter a two-digit number in the Authenticator on the mobile device, which is then displayed on the PC.
Conversely, this means that if an attacker has captured the credentials, he still cannot type in the number on the mobile device and will continue to be locked out. The user receives the prompt and is automatically made aware that something is wrong.
The configuration can be done in Azure AD [note: while this article is being written, the rollout of Microsoft Entra is taking place, so the screenshots are already branded with MS Entra]:

Here in the menu, of course, the Authenticator should be enabled for all users. The authentication methods can be set as desired – Any is recommended to keep the option for passwordless login open for the employees:

The important settings for number matching are then hidden in the other options. These will be activated automatically for everyone from the end of February 2023, but it is recommended to do so now:

As a result, the user receives a prompt to type in the mentioned two-digit number at the next MFA-based login. Microsoft has described this very nicely in this article and also illustrated it.
Door 13 (13.12.2022) – Security Baseline part 2: Conditional Access
After we discussed MFA behind door number 12, the question naturally remains how and in which scenarios this should be enforced. There could also be scenarios in which MFA is explicitly not desired. In order to be able to map these questions, Microsoft has created Conditional Access. Conditional Access is based on the following principle: Every logon must be confirmed / performed in Azure AD, so the AAD can also be used to regulate logons.
This regulation takes place with Conditional Access. Conditional Access is thus something like the ‘firewall’ for authentication attempts. However, Conditional Access has a different approach than conventional firewalls:
| While you explicitly allow traffic at a classic firewall, Conditional Access is a tool to lock it down! Azure AD allows all types of logins by default, with Conditional Access the unwanted logins are restricted or prohibited |
As a company, you therefore have to think about how you want to limit the logins to your own tenant. The following regulations have established themselves as a basis:
- Exclude all registration attempts from countries with which there is no business relationship
- Enforce MFA for admins
- Enforce MFA when accessing the Azure Portal
- Logins of all users require either MFA or an enterprise device
- Exclusion of all platforms not used in the company (e.g. Linux and macOS)
Disabling of obsolete protocols with basic authentication (e.g. POP3, IMAP4, Exchange ActiveSync)
- Requires use of ‘approved’ client apps on mobile devices (these are apps that Microsoft confirms are secure and configurable by policy).
However, these regulations can be used not only for internal employees, but also for accesses by external parties who are invited to your own tenant, so-called guest accounts. Here, too, there are some best practices:
- Use of ‘approved’ client apps on mobile devices required
- MFA is always required
- Consent to terms of use is obtained regularly (e.g. every 180 days)
Microsoft now also offers many good templates in the Conditional Access Portal. These are definitely worth a look:

There are more things and more possibilities with Conditional Access, for example, a forced password change at the user based on metrics in Azure AD that determine how likely it is to be an attack attempt. Such features are included in the Azure AD Premium P2 license. All the features described above can already be used with the smaller Azure AD Premium P1.
You need help with license procurement or your conditional access ruleset – contact us!
Door 14 (14.12.2022) – Emergency Accounts
Emergency accounts are nowadays part of a watertight zero-trust concept. These come into play if other security measures fail or there is a large-scale failure in the cloud services. In this way, customers keep a back door open to their own environment.
Emergency accounts are often referred to as break-the-glass accounts. These must of course be exempt from all conditional access rules and should be the only accounts that have permanent global admin rights in the tenant. Therefore, 3 things are essential for emergency accounts:
- The password should be system generated and at least 128 characters long
- The password should not be stored in a password manager accessible to everyone
- The login attempts of an emergency account must not only be logged, there should be immediate alerting
- As a company, a regular K-case test must be carried out that the accesses work and likewise the alarming
Microsoft currently recommends maintaining 2 emergency accounts in the tenant. The monitoring of these can be implemented relatively easily via LogAnalytics. An Azure subscription is required for this. Microsoft has documented this procedure in the TechCommunity, among other places.
Feel free to contact us for assistance in configuring your emergency accounts, we have already secured a large number of tenants this way.




